In today’s age, cyber threats have become a continuous and growing challenge for individuals and organizations. As technology advances, so do the methods employed by cybercriminals. Understanding the most common types of cyber attacks and how to protect against them is important for protecting your personal and professional data.
In this post, we will give you the Top 5 Cyber Attacks You’re Most Likely To Face and how you can protect yourself from not falling for these attacks.
What are Cyber Attacks?
Cyber attacks involve individuals or groups intentionally breaching information systems. They steal, alter, or destroy data, disrupt operations, or use compromised systems for further malicious activities.
These attacks can target governments, businesses, and private individuals, ranging from simple phishing scams to complex state-sponsored spying.
Cyber attackers have various motivations, such as financial gain, political objectives, personal vendettas, or creating chaos. As we depend more on digital technologies, it’s important to understand and reduce the risks of cyber attacks to protect sensitive information.
What are the Top 5 Cyber Attacks?
There are many different types of cyber attacks that target individuals, businesses, and governments, each varying in method, complexity, and effect. Here are the top 5 Cuber Attacks that You’re Most Likely To Face.
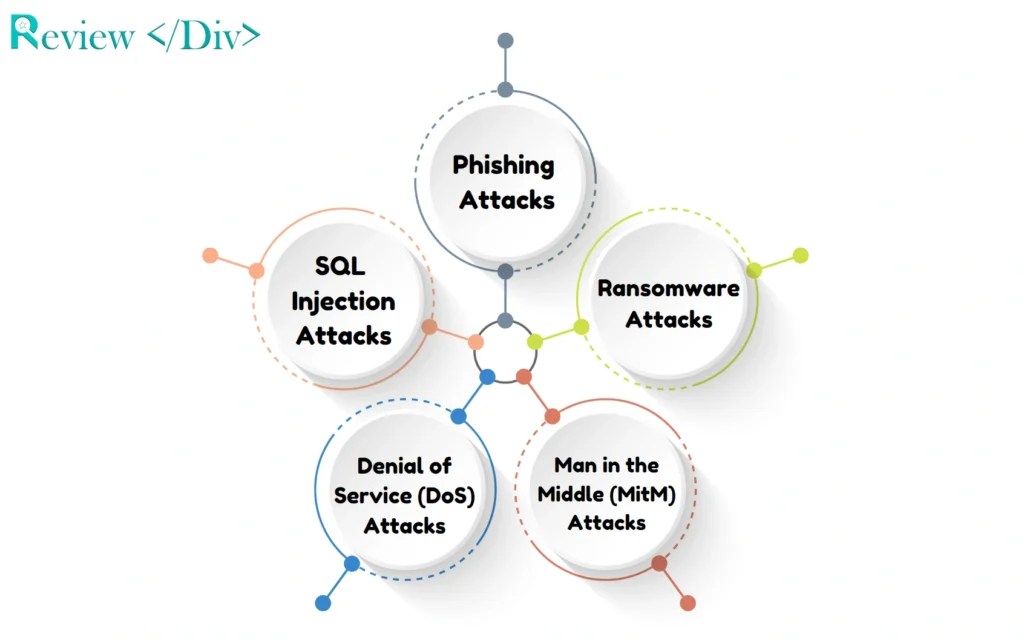
- Phishing Attacks
- Ransomware Attacks
- Man-in-the-Middle (MitM) Attacks
- Denial-of-Service (DoS) Attacks
- SQL Injection Attacks
1. Phishing Attacks
Phishing attacks are one of the most general and effective forms of cybercrime. They involve tricking individuals into revealing sensitive information such as usernames, passwords, and credit card details by acting as a trustworthy entity in electronic communications. Here’s how it works.

Creates Fake messages: Attackers create deceptive messages that appear to be from a legitimate source, such as a bank, a popular website, or a trusted organization. These messages look very convincing, mimicking the logos, language, and design of the real entity.
Delivering the message: The attackers send these messages via email, text messages, or social media. They target a broad audience, hoping that some recipients will fall for the deception.
Attracting the Victim: The message contains a sense of urgency or a compelling reason to click on a link or download an attachment. Common tricks include warnings about account security, urgent requests for personal information, or attractive offers and discounts.
Capturing Information: When the victim clicks on the link, they are directed to a fake website that looks like a legitimate site. Here, they are prompted to enter sensitive information, such as usernames, passwords, credit card numbers, or other personal details.
Using the Data: The attackers capture this information and use it for malicious purposes. They may steal money, commit identity fraud, or sell information on the dark web. In some cases, the attackers install malware on the victim’s device to gain further access to personal data or control the device.
2. Ransomware Attacks
Ransomware attacks involve malicious software that encrypts a victim’s files or locks them out of their system until a ransom is paid. Once the ransomware infects a computer or network, it makes data inaccessible, and attackers demand payment. This type of attack can target anyone, from individual users to large organizations.
The impact of ransomware attacks can be severe, causing significant financial loss and disruption. For individuals, it can mean losing personal files and sensitive information. Here’s how it works.

Delivery Methods: Attackers deliver ransomware through phishing emails, malicious websites, or software vulnerabilities. These methods trick users into downloading and executing the ransomware on their systems.
Encryption of Files: Once executed, the ransomware begins to encrypt files on the target system, making them inaccessible to the user. This encryption ensures that the victim cannot access their data without the decryption key.
Ransom Demand: After encryption, the victim receives a ransom note demanding payment in cryptocurrency. The note instructs the victim on how to pay the ransom to receive the decryption key needed to unlock their files.
3. Man-in-the-Middle (MitM) Attacks
A Man-in-the-Middle (MitM) attack is a type of cyber attack where an attacker secretly intercepts and relays communications between two parties who believe they are directly communicating with each other.
The attacker effectively places themselves in the middle of the transaction or communication, hence the name. This type of attack can compromise the confidentiality, integrity, and authenticity of the information being exchanged. Here’s how it works.

Interception: The attacker intercepts the communication between two parties. This can be done through various means, such as compromising a Wi-Fi network, using DNS spoofing, or hijacking a session.
Eavesdropping: Once the communication is intercepted, the attacker can monitor the information being exchanged. This includes sensitive data like login credentials, personal information, or financial transactions.
Manipulation: The attacker can also alter the communication, inject malicious content, change the data, or redirect the parties to malicious websites. This can lead to further attacks, such as malware infections or additional data breaches.
4. Denial-of-Service (DoS) Attacks
A Denial-of-Service (DoS) attack makes a computer, network, or service unavailable to its intended users by crushing it with excessive requests or data.
This flood of traffic disrupts normal operations, causing the system to slow down or crash. Here’s how it works.
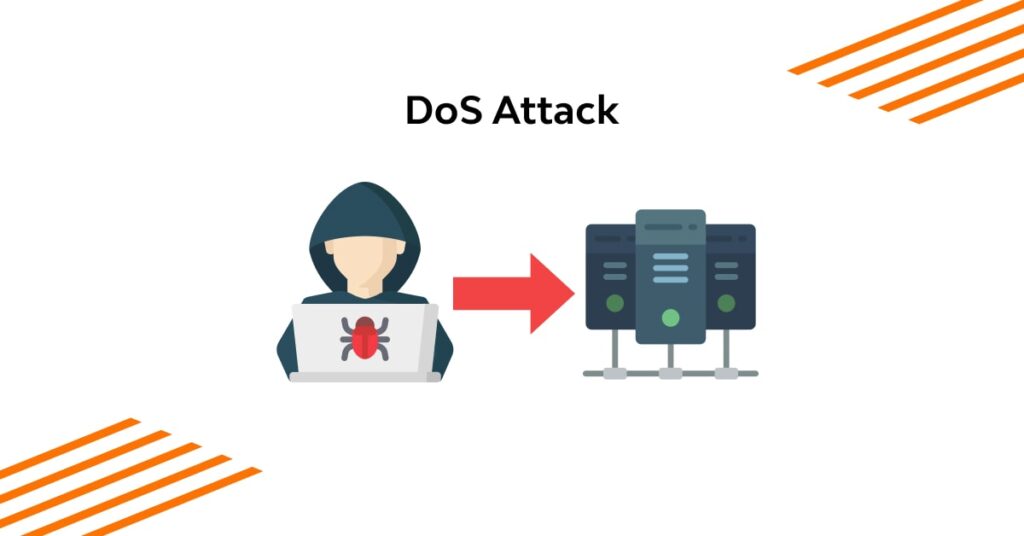
In a DoS attack, the attacker sends a massive amount of traffic or requests to a target system. This can saturate the network bandwidth, consume server resources, or control system vulnerabilities. The excessive load prevents legitimate users from accessing the service or data.
Types of DoS Attacks:
- Volume-Based Attacks: These involve flooding the target with a high volume of traffic, such as sending huge amounts of data packets to consume network bandwidth.
- Protocol Attacks: These control weaknesses in network protocols to disrupt service. For example, sending malformed packets that exploit flaws in network protocols.
- Application Layer Attacks: These target specific applications or services, like sending a large number of requests to a web server to exhaust its resources.
5. SQL Injection Attacks
SQL injection is a code injection technique that uses vulnerabilities in an application’s software to gain unauthorized access to the database. This can lead to data breaches, data loss, and unauthorized data manipulation.
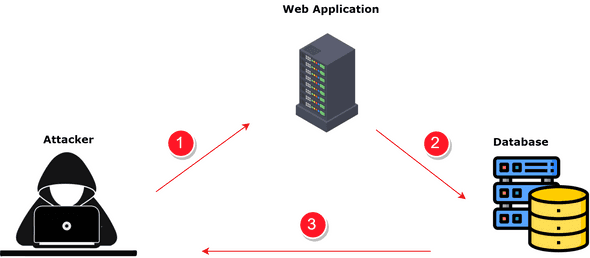
SQL injection attacks exploit vulnerabilities in an application by injecting malicious SQL code into input fields like login forms or search boxes. When the application passes this input to the database server, the malicious code is executed.
This unauthorized code execution allows the attacker to retrieve, modify, or delete data, bypassing standard security measures. By this, attackers can gain unauthorized access to sensitive information and manipulate or compromise the database.
How to protect yourself from these Cyber attacks?
To protect yourself from these Cyber attacks and more types of attacks, here are some tips that you should follow.
1. Use Strong and Unique Passwords
Creating and maintaining strong, unique passwords for each of your accounts. A strong password should be at least 12 characters long and include a mix of upper and lower case letters, numbers, and special characters.
2. Enable Multi-Factor Authentication (MFA)
Multi-factor authentication adds an extra layer of security by requiring more than just a password to access an account. This involves a second form of verification, such as a code sent to your mobile device or generated by an authentication app.
3. Keep Software and Systems Updated
Regularly updating your software, operating systems, and applications is crucial in protecting against cyber threats. Updates and patches include security fixes for vulnerabilities that cybercriminals can use.
4. Use Antivirus and Anti-Malware Software
Installing reputable antivirus and anti-malware software on your devices provides an essential layer of defense against malicious software. These programs are designed to detect, block, and remove a wide range of threats, from viruses to spyware.
5. Use Virtual Private Networks (VPNs)
Using a Virtual Private Network (VPN) when accessing the internet, especially on public Wi-Fi, encrypts your data and hides your IP address, making it more difficult for cybercriminals to intercept your online activities.
FAQs
A phishing attack is a type of cyber attack where attackers impersonate a legitimate entity to trick you into revealing sensitive information, such as usernames, passwords, or financial details.
To recognize a phishing attack, look for signs such as misspelled email addresses, urgent or threatening language, suspicious links or attachments, and requests for personal information.
To protect yourself from ransomware attacks, regularly back up your data to an external drive or cloud storage, keep your software and operating systems updated with the latest security patches, use reputable antivirus and anti-malware software
To prevent MitM attacks, avoid using public Wi-Fi for sensitive transactions, use a Virtual Private Network (VPN) for encrypted connections, ensure websites use HTTPS, and implement strong encryption protocols.
SQL injection is a type of attack where malicious SQL code is inserted into input fields to access or manipulate a database.
To protect your website from SQL injection, use parameterized queries and prepared statements to handle user inputs securely, implement input validation and sanitization to filter out harmful data, and regularly update your database management systems to address known vulnerabilities.
Laura Kemmis is a passionate trendsetter and reviewer, dedicated to researching the latest scams and frauds while sharing her insights with the world. She provides valuable information to keep her audience aware and informed about the latest scams. Additionally, Laura discovers and analyzes trends in fashion, technology, and lifestyle, offering a fresh and honest perspective in her reviews.