In today’s age, technology is important to our daily lives, but it has also given rise to tech support scams, a major danger to consumers globally. Cybercriminals pretending to be legitimate tech support representatives use individual’s fears of computer viruses, hacking, and technical issues.
This article explores the methods used in tech support scams, the possible effects on victims, and essential steps to protect oneself from these fraudulent schemes.
What are Tech Support Scams?
Tech support scams are fraudulent schemes where scammers copy legitimate technical support services to trick victims into believing their devices have issues that need immediate attention.
These scammers contact victims through unsolicited phone calls, emails, or pop-up messages on their computers. They claim to be from well-known tech companies and claim that the victim’s computer is infected with a virus, compromised by hackers, or experiencing other critical problems.
Here are some examples of fake messages used in tech support scams.
- “Your computer is infected with a virus! Call 1-800-123-4567 immediately for assistance.”
- “Alert: Your system has detected multiple threats. Contact Microsoft Support.”
- “Critical security warning! Your computer is at risk. Call our toll-free number now: 1-855-000-1111.”
- “Your account has been suspended due to suspicious activity. Click here to verify your details.”
- “Immediate action required! Your device has been compromised. Call 1-877-543-2100 for support.”
Once they have gained the victim’s trust, the scammers ask for remote access to the victim’s computer to fix the problem. During this process, they install malicious software, steal personal information, or manipulate the victim into paying for unnecessary services or software.
These scams can lead to significant financial loss and compromise the victim’s personal data. It is important to be careful of unrequested tech support offers and to verify the legitimacy of any technical support service before providing access to personal devices or sensitive information.
Common Types of Tech Support Scams
There are many types of Tech support scams used by scammers to trick users and scam them. Here are some common types of scams.
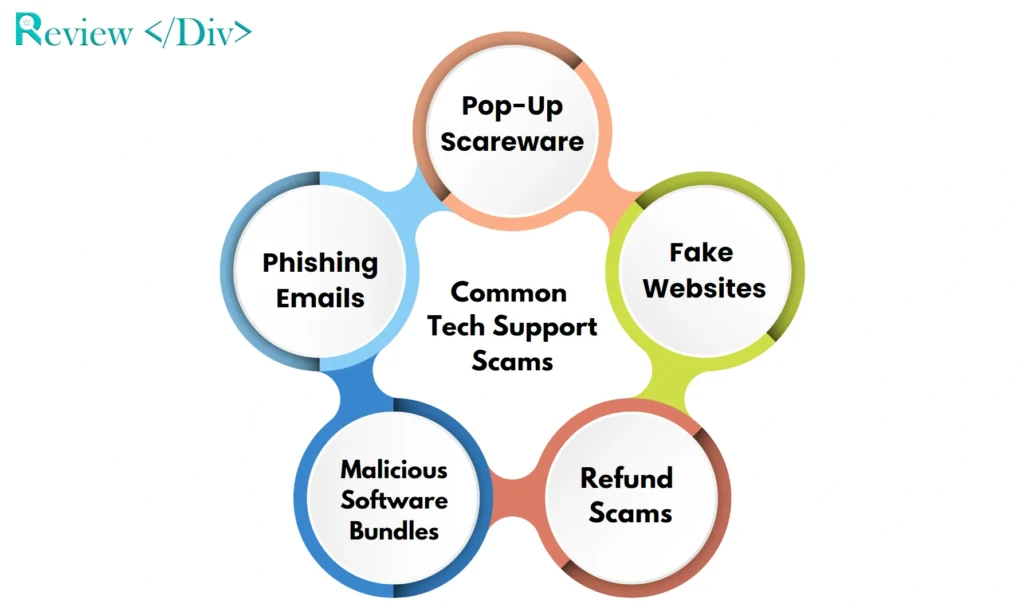
1. Pop-Up Scareware
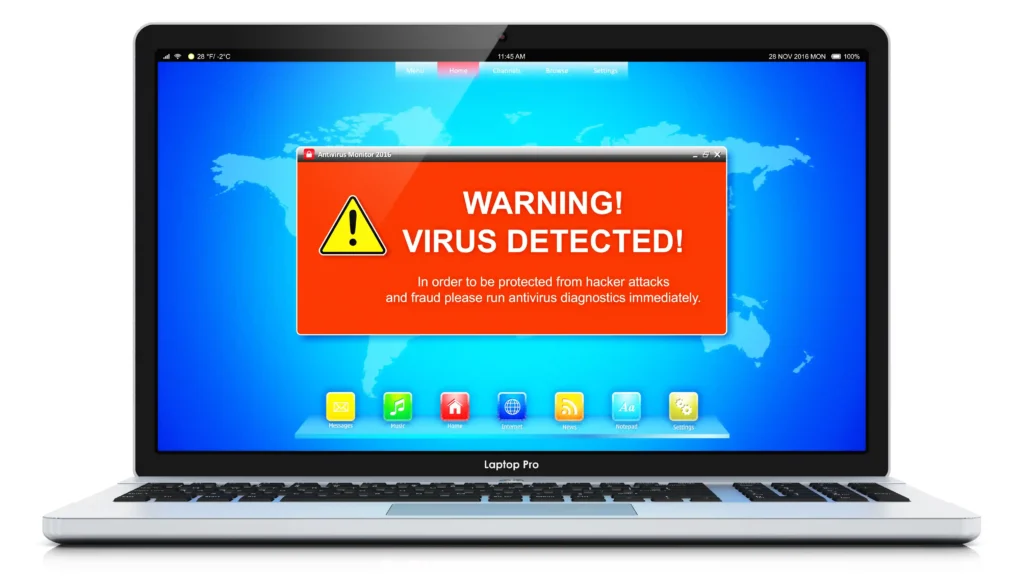
You might experience a pop-up message on your computer that warns of viruses or malware infections. The message urges you to call a toll-free number for immediate assistance. These pop-ups are fake, designed to scare you into paying for unnecessary services.
2. Fake Websites
Scammers create websites that look like legitimate tech support pages. These sites are optimized to appear in search engine results when users seek tech help. Once you land on one of these sites, they prompt you to call a number or provide personal information.
3. Phishing Emails
Scammers send emails that appear to be from tech companies, warning about security threats or account issues. They urge you to click on a link or download an attachment, which contains malware or leads to fake websites.
4. Malicious Software Bundles
Some free software downloads come bundled with adware, spyware, or fake system optimizers. These programs claim to fix issues but cause harm. Scammers then offer paid versions to “resolve” the problems.
5. Refund Scams
Scammers contact victims claiming they overpaid for tech services or software licenses. They promise refunds and ask for bank details or remote access. Instead of issuing a refund, they steal sensitive information.
How Scammers Trick You into Paying for Fake Services?
Tech support scams are tricky tactics used by scammers to force individuals into paying for unnecessary technical support services. These scams use various methods to deceive victims.
Phone Calls: Scammers copy technicians from reputable companies, claiming they have detected a problem with your computer. They request remote access to your device and then demand payment to resolve a nonexistent issue.
Pop-Up Warnings: Scammers create fake pop-up messages that appear on your computer screen, copying error alerts from your operating system or antivirus software. These warnings claim a security threat and provide a phone number for assistance.
Online Ads and Search Results: Scammers use search results to display their websites when you look for tech support online.
What to do if you fall for Tech Support Scams?
If you realize that you have fallen victim to a tech support scam, it is important to take the right steps to minimize damage.

- The first step is to disconnect your device from the internet immediately to prevent the scammer from continuing to access your system.
- If you provided remote access to your computer, shut it down and restart it in safe mode to begin addressing any installed malicious software.
- Running a complete scan with a reputable antivirus or anti-malware program can help detect and remove any threats that may have been introduced.
- Contact your bank or credit card company to report the fraud and cancel any payments you may have made. Inform them of the scam and follow their instructions to secure your accounts, including monitoring for unauthorized transactions.
- If you share personal information, such as passwords or sensitive data, change your passwords immediately for all affected accounts. Use strong, unique passwords and consider enabling two-factor authentication for added security.
- Report a complaint with the Federal Trade Commission (FTC) and report the incident to the Internet Crime Complaint Center (IC3).
- Providing detailed information about the scam can help other organizations track and stop fraudulent activities. Also, inform your friends and family about the scam to prevent them from becoming victims.
How Do Tech Support Scammers Reach You?
Tech support scammers use various strategies to reach victims, they want to trick and extract personal information or money.
One common method is through phone calls, where scammers pose as IT technicians or cybersecurity experts. They call unexpectedly, claiming to be from reputable companies. By building trust, they convince you to give remote access to your system or provide personal information like passwords.
Another tactic is sending phishing emails that appear to come from legitimate sources. These emails might state that your account has been suspended or that there is an issue requiring immediate attention, often related to a previous IT repair.
It’s important to remember that legitimate tech companies will not contact you unexpectedly about computer problems. Real security warnings will never ask you to call a phone number or click on a link.
What to do If you Get a Tech Support Scammer Call?
If you receive a call from a tech support scammer or any other scammer, it’s important to take the following steps to protect yourself from the fraud.
1. Hang Up Immediately
Do not engage in conversation or provide any personal information, such as your passwords or financial details. Scammers use high-pressure tactics and convincing scripts to manipulate you, so it’s important to stop communication as soon as possible.
2. Do Not Return the Call
Avoid calling back the phone number given by the scammer. This number is part of their scheme, and returning the call may lead to additional attempts to trick you or even further fraud. It’s best to avoid any further interaction with the scammer.
3. Ignore Fake Pop-Up Warnings
If you experience pop-up messages on your computer claiming there is a necessary security issue, do not click on any links or call the provided number. These pop-ups are designed to look like legitimate alerts but are usually fake and intended to scare you.
4. Verify the Source
If you have any doubts about the legitimacy of a tech support call, independently verify the organization’s identity. Examine the company’s official website or contact them directly using a phone number or email address you find from a reliable source.
5. Report the Incident
Reporting the scam is an important step in preventing further fraud. You can file a complaint with the Federal Trade Commission (FTC) at ftc.gov/complaint. This helps authorities gather information on fraudulent activities, track scammers, and take action to protect others from similar scams.
What Scammers Do with Stolen Money and Information?
Scammers use stolen credit card numbers, bank account details, or Social Security numbers to make unauthorized purchases, transfer funds, or drain victims’ accounts.
Victims of cryptocurrency fraud can lose significant amounts of money, as scammers attract them into repeated investments, leading to substantial financial losses. Scammers transfer stolen funds to different accounts to cover the money trail.
Stolen personal data is valuable and can be sold to marketing firms, spammers, and other cyber criminals. Hackers use stolen emails for phishing attacks, spreading malware, and social engineering.
How to Remove Malware from your Device?
Malware, or “malicious software,” refers to any type of software designed to harm, use, or otherwise compromise a computer system, network, or device.

Its primary purpose is to, damage, or gain unauthorized access to systems, steal personal information, or cause other forms of damage.
1. Windows PC
- Open the Windows Security settings.
- Navigate to Virus & Threat Protection.
- Select Scan options.
- Choose Microsoft Defender Antivirus (offline scan) and initiate a scan.
- Review the scan results in the Protection history.
If Malware is Severe:
- Restart your PC in Safe Mode and perform a scan using your antivirus software.
- Consider using a bootable antivirus tool, such as Norton, to scan your system.
- For continuous malware, you need to securely erase and reformat your boot drive and then reinstall a fresh copy of Windows.
2. Mac
- Disconnect from the internet and restart your Mac in Safe Mode.
- Open Activity Monitor to check for any suspicious applications running.
- Run a malware scanner to identify and remove threats.
- Once online again, clear your browser cache and history to remove any residual malicious data.
3. Android
- Boot your device into Safe Mode.
- Locate and uninstall any suspicious or malicious apps.
- Use a trusted anti-malware app (such as MalwareFox) to scan for and remove any remaining threats.
How to Protect yourself from Tech Support Scams?
Tech support scams can be highly tricky, but there are several steps you can take to protect yourself from these scams.
Unexpected Calls: If you receive an unexpected call from someone claiming to be tech support, hang up. Legitimate companies do not make unsolicited support calls.
Direct Contact: If you receive a tech support call, email, or message, contact the company directly using a known, official number or website.
Unauthorized Access: Never give remote access to your computer to someone who contacts you unexpectedly. Scammers use this access to steal your information or install malware.
Antivirus Programs: Use reputable antivirus and anti-malware software to protect your devices. Confirm it is always up-to-date.
Bank and Credit Card Statements: Regularly check your financial statements for unauthorized transactions. Report any suspicious activity to your bank or credit card company immediately.
Improved Security: Allow multi-factor authentication (MFA) on your accounts for an extra layer of security. This makes it harder for scammers to access your accounts even if they obtain your login credentials.
FAQs
To stop tech support scams, be skeptical of unsolicited calls, emails, and pop-up messages, never grant remote access to unknown parties, and verify tech support requests through official company contact information. Regularly update your security software and enable multi-factor authentication on your accounts.
One common tactic in tech support scams is unsolicited phone calls, where scammers impersonate technicians from reputable companies, claiming they have detected a problem with your computer and requesting remote access.
Tech support scams involve fraudsters posing as legitimate technical support, using tactics like unsolicited calls, deceptive emails, and fake pop-up messages to convince victims and demand payment.
Signs of a tech support scam include unsolicited calls or messages claiming your device has a problem, requests for remote access to your computer, and demands for immediate payment to fix non-existent issues.
Millions of people fall for tech support scams each year. The Federal Trade Commission (FTC) reported that consumers lost over $55 million to these scams in 2020 alone.
Older adults and individuals with limited digital literacy often lose the most money to scams. They are frequently targeted by scammers due to less familiarity with online security practices.