These days, mobile threats are rising rapidly, posing serious risks for both individuals and businesses. As mobile devices become more common, they attract more cybercriminals who are always finding new ways to use their weaknesses.
The 2024 Mobile Threat Landscape Report highlights the growing danger and the critical need for strong mobile security to protect important information and more.
Increase in Mobile Threats
Mobile cyberattacks have flooded by 350% in 2023, driven mainly by the rise in remote work, which has provided more opportunities for cybercriminals.
This trend has continued into the first quarter of 2024, with more cases of mobile phishing, malware, and other threats. These developments highlight the need for stronger mobile security measures to protect against these growing risks.
Key Points From Q1 2024
The Q1(Quarter one) 2024 Mobile Threat Landscape Report highlights important trends and threats.
Phishing Attacks: Phishing attacks on mobile devices have tripled since last year. Cybercriminals are using more advanced tactics to trick users, making it easier for them to steal credentials and breach security.
Malware Increase: There’s been a significant rise in mobile malware, especially management tools that threaten both personal privacy and business data security. These malware types are becoming harder to detect.
App Vulnerabilities: Mobile apps, mostly browsers, are regular targets due to their weaknesses. Attackers are taking advantage of flaws in popular frameworks like WebRTC and the V8 engine, highlighting the importance of regular updates and timely patches.
Major Mobile Threats in 2024
The mobile threat landscape is dominated by several key threats that continue to grow and challenge cybersecurity defenses.
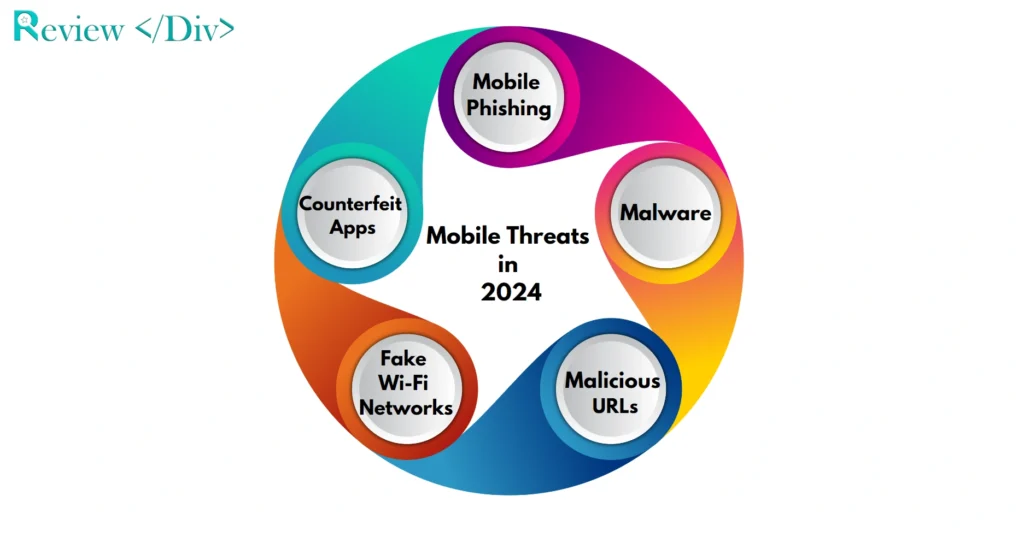
1. Mobile Phishing
Mobile phishing has become one of the most widespread threats, with a new phishing site emerging every 20 seconds. Notably, 85% of these attacks occur outside of traditional email platforms, using SMS, social media, and other communication channels.
2. Malware
The range of mobile malware, including spyware, ransomware, and adware, is expanding, with these malicious programs aggressively targeting user data and disrupting business operations.
3. Malicious URLs
Cybercriminals are using HTTPS certification and Punycode attacks to create convincing phishing websites, making it increasingly difficult for users to identify malicious links.
4. Fake Wi-Fi Networks
Attackers are setting up rogue Wi-Fi hotspots in public spaces to intercept sensitive data from unsuspecting users, posing a significant risk to both individuals and organizations.
5. Counterfeit Apps
Counterfeit apps, found even in official app stores, pose serious risks as they frequently request extensive permissions that can be exploited to access sensitive user information.
The Role of Social Engineering
Social engineering has become a popular strategy among cyber criminals. In these attacks, scammers pretend to be trusted individuals, such as IT support personnel, to trick people into giving away sensitive information.
This approach has changed the way cyberattacks happen, making it essential for organizations to teach their employees how to spot and handle phishing attempts.
By understanding these tactics, employees can better protect themselves and their organization from falling victim to such schemes.
Risks in Mobile Systems and Apps
The report highlights the need to address risks in mobile operating systems and apps. Multiple zero-day flaws have been found in essential components like the V8 engine and WebRTC framework, which are used in mobile browsers.
These issues remain risky until patches are released and applied. Mobile browsers are targeted by cyberattacks. Malicious links use known vulnerabilities, making browser security a major concern.
There is a delay between when security patches are released and when they are installed on devices. This gap creates opportunities for attackers, making effective patch management important.
How To Strengthen Mobile Security Measures?
To counter the growing threats, organizations must execute complete mobile security strategies. Here are the key components that can help you Strengthen Mobile Security Measures.
1. Advanced Mobile Threat Defense
Applying sophisticated mobile threat defense solutions can help detect and reduce threats in real time. Solutions like Lookout provide built-in protections against phishing and other malicious activities.
2. User Training and Awareness
Regular training programs for employees on mobile security best practices, including how to recognize and avoid phishing attempts, are vital for reducing the risk of successful attacks.
3. Risk Management
Continuous monitoring and timely remediation of risks in mobile applications and operating systems are important to maintaining a secure mobile environment.
4. Multi-Factor Authentication (MFA)
Implementing MFA adds an extra layer of security, helping to prevent unauthorized access to mobile devices and sensitive data.
Future Trends in Mobile Security
As mobile threats keep increasing, several trends are likely to shape the future of mobile security. Here are the future trends in Mobile Security.
Stricter Regulations: As cyberattacks increase in frequency and severity, regulatory bodies are expected to impose more stringent compliance requirements on organizations, particularly concerning data protection and breach notification.
Adoption of Emerging Technologies: The use of artificial intelligence (AI) and machine learning (ML) in mobile security solutions is expected to grow, improving the ability to detect and respond to new and growing threats.
Focus on Privacy: With growing concerns over user privacy, organizations will need to prioritize data protection measures to maintain customer trust and comply with increasingly stringent regulations.
FAQs
Mobile system vulnerabilities are weaknesses or flaws in mobile operating systems or apps that can be exploited by cybercriminals to gain unauthorized access or cause harm.
You can check for vulnerabilities by keeping your app updated, using security tools, and reviewing security reports for any known issues.
The report identifies key threats including mobile phishing, rising malware variants, vulnerabilities in mobile apps and browsers, and risks from rogue Wi-Fi hotspots and counterfeit apps.
Organizations can enhance protection by implementing advanced mobile threat defense solutions, conducting regular employee training, managing vulnerabilities effectively, and using multi-factor authentication.
Social engineering is a tactic where attackers deceive users into revealing sensitive information or credentials. The report notes that this technique is increasingly used in mobile phishing attacks.
Mobile phishing can lead to unauthorized access to personal or organizational data, financial losses, and identity theft. It is a growing concern as attackers use more convincing tactics.